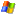SXE - Framework Overview
|
| Policy Rule Set | Enforced by | Items controlled | Examples |
|---|---|---|---|
| Mandatory Access Control (MAC) file system | The MAC enabled Linux kernel | entities on the file system |
|
| Mandatory Access Control (MAC) capabilities | The MAC enabled Linux kernel | system capabilities |
|
| Application rule-sets | the Safe Execution Environment system | requests for service |
|
The function of the MAC-enabled Linux kernel is to prevent processes from accessing some parts of the system, for example:
- /dev entries
- binary libraries
- configuration files.
The MAC rule-set can, if needed, allow such access under read-only provisions or deny access altogether. The MAC can also prevent certain system calls via kernel capabilities, such as CAP_SYSADMIN and CAP_RAWIO.
The SXE employs the sandbox MAC rule set which inverts the usual system of allow, unless specifically denied to instead be deny, unless specifically allowed. The sandboxing provided by the MAC kernel patches and its rule-set provides a broad low-level degree of protection against system-level risks from flawed or malicious programs attempting to access system resources. For example, any alteration of data or password files, harvesting of user information, and installation of root-kits is prevented.
At the application level, SXE acts like a firewall to prevent programs making unauthorized access to sensitive system services. Requests received by the phone server are first checked to see if the originating program has the correct security domain awarded to allow the sending of such messages.
During the package download process, the user is presented with a confirmation dialog with an easily understood description of the domain under which the package will operate. If approved, the Qt Extended package installation facility is responsible for applying the appropriate rules to a package.
If an application violates policy such as making a service request or opening a file that it is not allowed to, the application is of course denied that access. The security monitor process known as SxeMonitor then acts to terminate the application and notify the user.
| Cette page est une traduction d'une page de la documentation de Qt, écrite par Nokia Corporation and/or its subsidiary(-ies). Les éventuels problèmes résultant d'une mauvaise traduction ne sont pas imputables à Nokia. | Qt qtextended4.4 | |
| Copyright © 2012 Developpez LLC. Tous droits réservés Developpez LLC. Aucune reproduction, même partielle, ne peut être faite de ce site et de l'ensemble de son contenu : textes, documents et images sans l'autorisation expresse de Developpez LLC. Sinon, vous encourez selon la loi jusqu'à 3 ans de prison et jusqu'à 300 000 E de dommages et intérêts. Cette page est déposée à la SACD. | ||
| Vous avez déniché une erreur ? Un bug ? Une redirection cassée ? Ou tout autre problème, quel qu'il soit ? Ou bien vous désirez participer à ce projet de traduction ? N'hésitez pas à nous contacter ou par MP ! | ||
Copyright © 2000-2012 - www.developpez.com