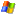SXE - Package Keying and Manifest
|
| Name | File | Runtime Access | Format | Function |
|---|---|---|---|---|
| Manifest | manifest | packagemanager, qpe | Binary file (sorted by dev_id, inode):
|
|
| Installs | installs | packagemanager, qpe | Text file (fields ':' separated, records LF separated):
|
|
Process keys and Program Identities
In order to decide which policy to apply when a service is requested, the Program Identity or progId is used. The progId is a key into the policy lookup table.
Conceptually a program is a binary (or binaries) on disk. When a package is installed its program binaries are copied into place in a directory on disk (or flash) storage to later be launched. One progId is used by all binaries of a package, since all binaries in the package have the same set of security domains.
When a program binary is launched as an instance, it is a process in execution. At that point it has a Unix process id or pid.
The process must transmit a Program Identity to request a service.
So that the server providing the service can know that the process is authorized to use that progId, the process must also transmit the Process Key or key.
The server can lookup to see if the key matches one of the keys allocated to that progId. This constitutes authenticating the process.
Key Propagation
In order for keys to work as an authentication mechanism, they must be a shared secret between the process, which is executing a given program, and the server, which is doing the authentication.
Here shared secret means that no other process can have the key; but both the client and server of the service must have it.
Achieving this state is not a trivial problem, but when it is achieved it makes authentication secure, simple and fast. No further lookup is required, since possession of the key guarantees authentication.
SXE achieves key propagation by relying on the LIDS kernel patch as modified for Qt Extended.
The client can read its key from /proc/1234/lids_key where 1234 is the Unix pid of that process. Keys are created in these pseudo files when the process is launched, and the kernel enforces that only the process itself (in this case process pid 1234) can read its own key.
This technique means that no LIDS rules are required to protect each key, since it is automatically exclusive to the process. Also problems relating to read only file systems are solved.
The server can read the keys for all processes from /proc/lids/keys. This pseudo file is updated by the kernel will the keys, and the device id and inode number of the binary. The pseudo file is protected by a LIDS MAC rule to prevent untrusted processes from reading it.
The Development Case
On the desktop development environment, the /proc/lids/keys pseudo file is not available, and nor are the per-process pseudo files, obviously because the desktop machine does not have the Qt Extended LIDS kernel patch.
In this case, a fallback method simulates the pseudo files by using on-disk files with the exact same format. These disk files are read by the server.
This is similar in concept to how instead of /dev/fb0 the virtual frame buffer is used on the desktop.
The files used in the development case are:
| Name | File | Runtime Access | Format | Function |
|---|---|---|---|---|
| Key sequence file | keyfile.sequence | packagemanager, qpe | Binary file (sorted by progId
|
|
| Process key file | keyfile | packagemanager, qpe | Binary file
|
|
For the clients to each know their key, in the development (not in the live) case, the key is embedded into the binary image of the file.
In general this method is not suitable to be used on the device, since in the case of read-only devices, the key is not able to be changed from the ROM image.
A malicious hacker who obtains a copy of the ROM image (eg by manually cracking a phone in his possession) can then know the keys for a large number of devices.
Best Of
Actualités les plus lues
- Pourquoi les programmeurs sont-ils moins payés que les gestionnaires de programmes ? Manquent-ils de pouvoir de négociation ? 42
- Qt Commercial : Digia organise un webinar gratuit le 27 mars sur la conception d'interfaces utilisateur et d'applications avec le framework 0
- Interfaces mobiles : nouveaux usages, nouvelles ergonomies, par Miratech 0
- Implémentation d'une table de hachage à référence faible avec Qt, un article de Christophe Dumez traduit par Thibaut Cuvelier 4
- « Quelque chose ne va vraiment pas avec les développeurs "modernes" », un développeur à "l'ancienne" critique la multiplication des bibliothèques 94
- Apercevoir la troisième dimension ou l'utilisation multithreadée d'OpenGL dans Qt, un article des Qt Quarterly traduit par Guillaume Belz 0
- Les développeurs ignorent-ils trop les failles découvertes dans leur code ? Prenez-vous en compte les remarques des autres ? 17
- Pourquoi les programmeurs sont-ils moins payés que les gestionnaires de programmes ? Manquent-ils de pouvoir de négociation ? 42
- Quelles nouveautés de C++11 Visual C++ doit-il rapidement intégrer ? Donnez-nous votre avis 10
- Adieu qmake, bienvenue qbs : Qt Building Suite, un outil déclaratif et extensible pour la compilation de projets Qt 17
- 2017 : un quinquennat pour une nouvelle version du C++ ? Possible, selon Herb Sutter 7

- Linus Torvalds : le "C++ est un langage horrible", en justifiant le choix du C pour le système de gestion de version Git 100
- Comment prendre en compte l'utilisateur dans vos applications ? Pour un développeur, « 90 % des utilisateurs sont des idiots » 229
- Quel est LE livre que tout développeur doit lire absolument ? Celui qui vous a le plus marqué et inspiré 96
- Apple cède et s'engage à payer des droits à Nokia, le conflit des brevets entre les deux firmes s'achève 158
- Nokia porte à nouveau plainte contre Apple pour violation de sept nouveaux brevets 158
- Quel est le code dont vous êtes le plus fier ? Pourquoi l'avez-vous écrit ? Et pourquoi vous a-t-il donné autant de satisfaction ? 83
- Le Draft final de la norme C++ 0X validé 181

Le blog Digia au hasard

Créer des applications avec un style Metro avec Qt, exemples en QML et C++, un article de Digia Qt traduit par Thibaut Cuvelier
Communauté
Ressources
- 91 cours et tutoriels Qt
- F.A.Q. Qt : 200 questions et réponses
- 48 Qt Quarterly, 35 Qt Labs et 22 Qt DevNet en français
- 43 outils Qt
- 99 sources Qt
- 26 binaires Qt
- 6 livres Qt et 9 critiques
- La documentation de Qt 4.7 en français : 157 classes, 70 concepts et 24 modules
- 3 certifications Qt
Liens utiles
Contact
- Vous souhaitez rejoindre la rédaction ou proposer un tutoriel, une traduction, une question... ? Postez dans le forum Contribuez ou contactez-nous par MP ou par email (voir en bas de page).
Qt dans le magazine
| Cette page est une traduction d'une page de la documentation de Qt, écrite par Nokia Corporation and/or its subsidiary(-ies). Les éventuels problèmes résultant d'une mauvaise traduction ne sont pas imputables à Nokia. | Qt qtextended4.4 | |
| Copyright © 2012 Developpez LLC. Tous droits réservés Developpez LLC. Aucune reproduction, même partielle, ne peut être faite de ce site et de l'ensemble de son contenu : textes, documents et images sans l'autorisation expresse de Developpez LLC. Sinon, vous encourez selon la loi jusqu'à 3 ans de prison et jusqu'à 300 000 E de dommages et intérêts. Cette page est déposée à la SACD. | ||
| Vous avez déniché une erreur ? Un bug ? Une redirection cassée ? Ou tout autre problème, quel qu'il soit ? Ou bien vous désirez participer à ce projet de traduction ? N'hésitez pas à nous contacter ou par MP ! | ||
Copyright © 2000-2012 - www.developpez.com